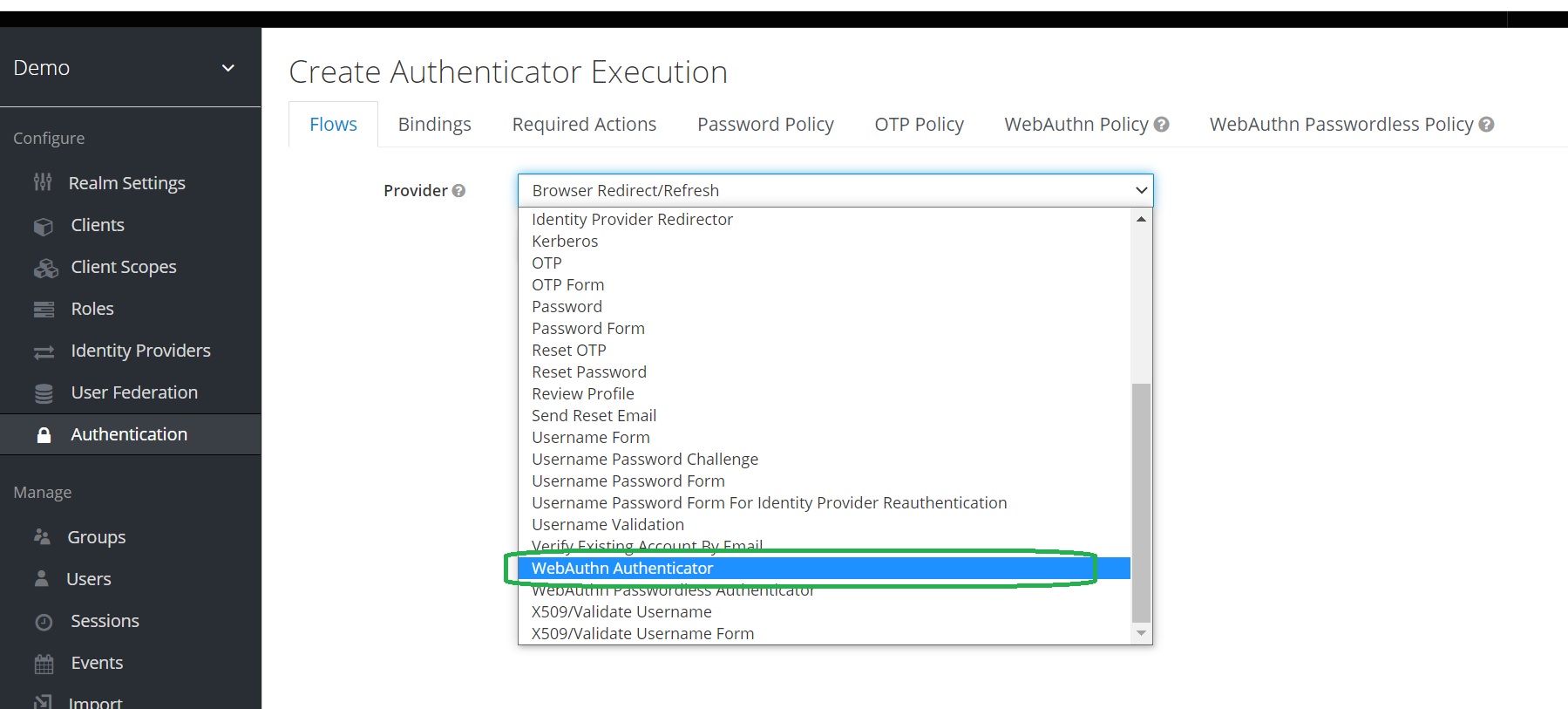
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog
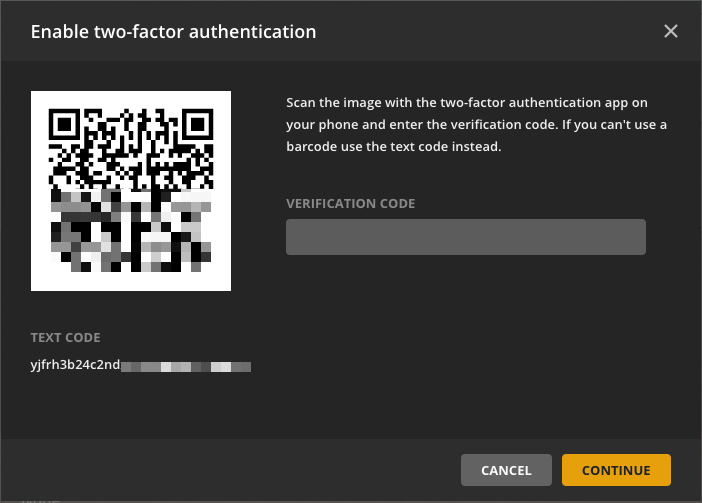
Secure Your Account with Two-Factor Authentication

Authentification Guide — Two authenticators
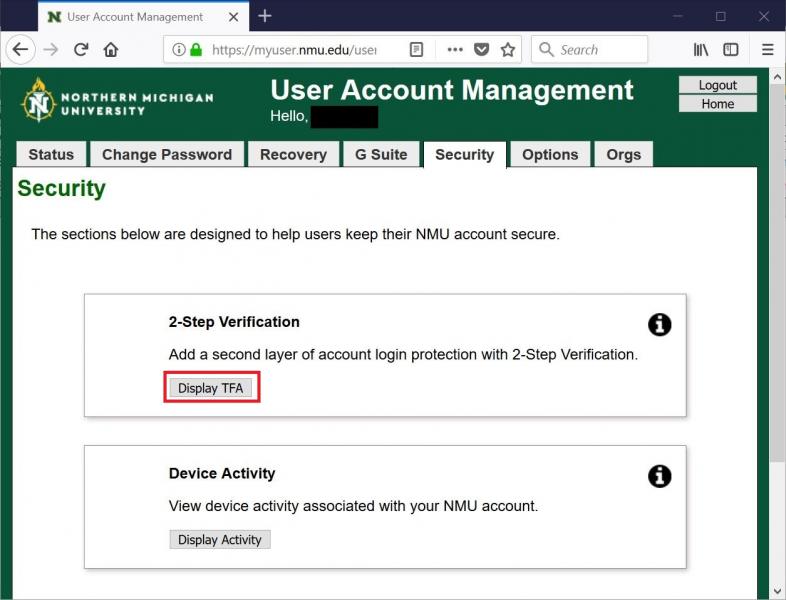
Using Google Authenticator for 2 factor authentication

Guide - Two-Factor Authentication: Methods and Myths

Two-factor authentication explained: How to choose the right level of security for every account

Client to Authenticator Protocol (CTAP)
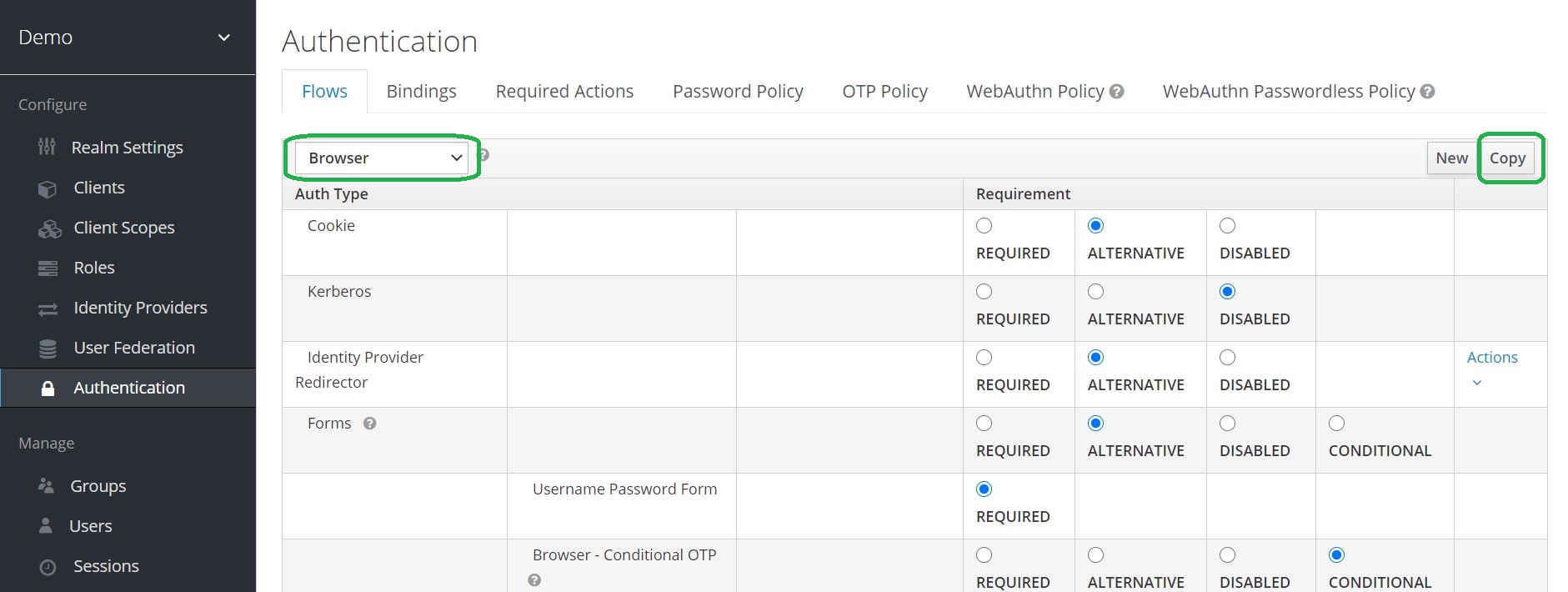
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog
Token2, Classic OATH hardware tokens for Office 365, Hardware token for Ubiquiti Account 2FA, TOKEN2 MFA Products and Services

FIDO2: Authenticate easily with phishing-resistant security - Help Net Security
